Proxy
A proxy is an intermediary piece of hardware/software that sits between a client (such as a web browser) and the destination server. It intercepts requests from clients and can modify, filter, or forward these requests to the target server, and then relay the response back to the client.
What Is a Proxy?
- Intermediary Role:
A proxy server acts as a middleman between the client and the server. Instead of communicating directly with the destination server, the client sends its requests to the proxy, which then handles the communication with the target server. This setup provides an additional layer between the client and the server. - Communication Handling:
Proxies can manage and inspect traffic, often applying rules such as caching, content filtering, or access control. They can transform requests and responses to meet specific requirements or policies.
Purpose of Proxy Servers
1 Security & Anonymity
A proxy can hide client identity from external servers.
What it provides:
- Hides the internal IP address.
- Prevents direct exposure of internal network
- Block malicious websites
- Scrubs or sanitizes requests
- Can rate-limit requests to prevent DoS-like behaviour
Use case examples:
- Corporate networks hides all internal user IPs.
- Making outbound calls to third-party APIs without exposing infrastructure.
2 Traffic Filtering & Access Control
Proxies act as gatekeepers.
They can:
- Block access to specific websites.
- Inspect content.
- Enforce organizational policies (e.g., no social media during office hours).
- Block suspicious domains.
Used by:
Corporations, universities, and governments for compliance or censorship.
3 Caching (Performance Optimization)
One of the biggest historical purposes of proxies.
Proxies can cache frequently requested data.
Benefits:
- Reduces latency for repeated requests.
- Saves bandwidth.
- Reduces load on backend servers.
Example:
- User requests image
banner.png. - Proxy caches it.
- Next time, it serves the image without contacting the backend server.
CDNs are essentially distributed caching reverse proxies.
4 Logging, Monitoring & Auditing
Proxies can ideal for observability.
A proxy can:
- Log all requests.
- Track user behaviour.
- Generate analytics.
- Monitor traffic patterns.
- Detect anomalies.
Security teams often user proxies for:
- Incident analysis
- Malware detection
- Traffic replay
5 Load Balancing Traffic
Many load balancers are simply advanced reverse proxies.
They:
- Forward inbound traffic to different backend servers.
- Apply health checks.
- Distributed load using algorithms.
6 Protocol Conversion
Proxies can translate between different protocols.
Example:
- Client speaks HTTPS
- Backend speaks HTTP
- Proxy performs SSL termination
7 Rate Limiting & Throttling
Proxies protect backends from overload.
They enforce limits such as:
- Max requests per second per IP
- Max concurrent connections
- Burst limits
Used in:
- API Gateways
- Cloud providers
- Public APIs
Types
There are two types of proxies:
1️⃣ Forward Proxy
A forward proxy, often called a proxy, proxy server, or web proxy is a server that sits in front of a group of client machines. When those computers make requests to sites and services on the internet, the proxy server intercepts those requests and then communicates with web servers on behalf of those clients, like a middleman.
It sits in between the client and the wider network. It is typically used by clients within a private network to access external resources. The server (destination) never directly sees the client.
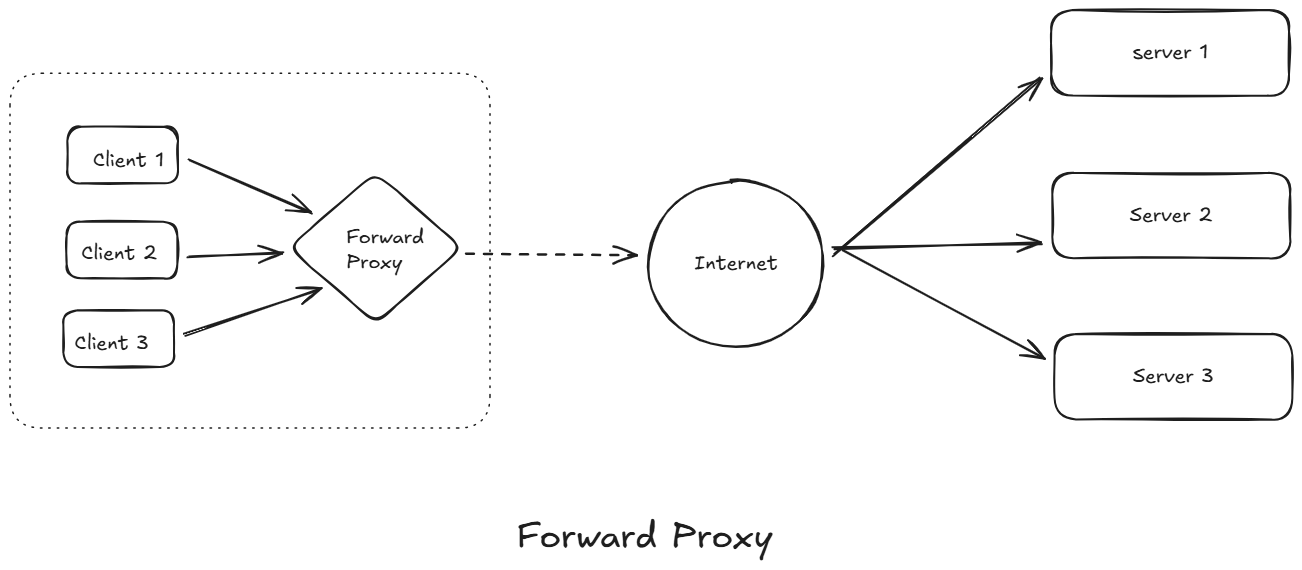
Use Cases:
- Access Control: Enforcing policies on what external sites users can access.
- Anonymity: Hiding the client’s IP address when accessing public resources.
- Caching: Storing copies of frequently accessed web pages to improve load times.
Why Do We Need a Forward Proxy?
1 Privacy & Anonymity
Proxy hides:
- Client IP
- Client device/network
E.g.,
Your browser -> proxy -> websites sees only proxy's IP.
2 Access Control
Companies block:
- YouTube
- Gambling sites
Proxy enforces corporate policies.
3 Caching
Proxy can cache:
- Images
- Videos
- Static files
Clients behind the same proxy get fast responses.
4 Rate Limiting / Throttling
Proxy limits outbound traffic
5 Security – Malware filtering
Proxy scans outgoing/incoming traffic.
2️⃣ Reverse Proxy
A reverse proxy is a server that sits in front of one or more web servers, intercepting requests from clients. When clients send requests to the origin server of a website, those requests are intercepted by the reverse proxy server.
The difference between a forward and reverse proxy is subtle but important. A simplified way to sum it up would be to say that a forward proxy sits in front of a client and ensures that no origin server ever communicates directly with that specific client. On the other hand, a reverse proxy sits in front of an origin server and ensures that no client ever communicates directly with that origin server.
It sits in front of one or more web servers. It receives requests from the internet and forwards them to the appropriate backend server.
Client -> Reverse Proxy -> Application ServersThe client thinks the reverse proxy is the server.
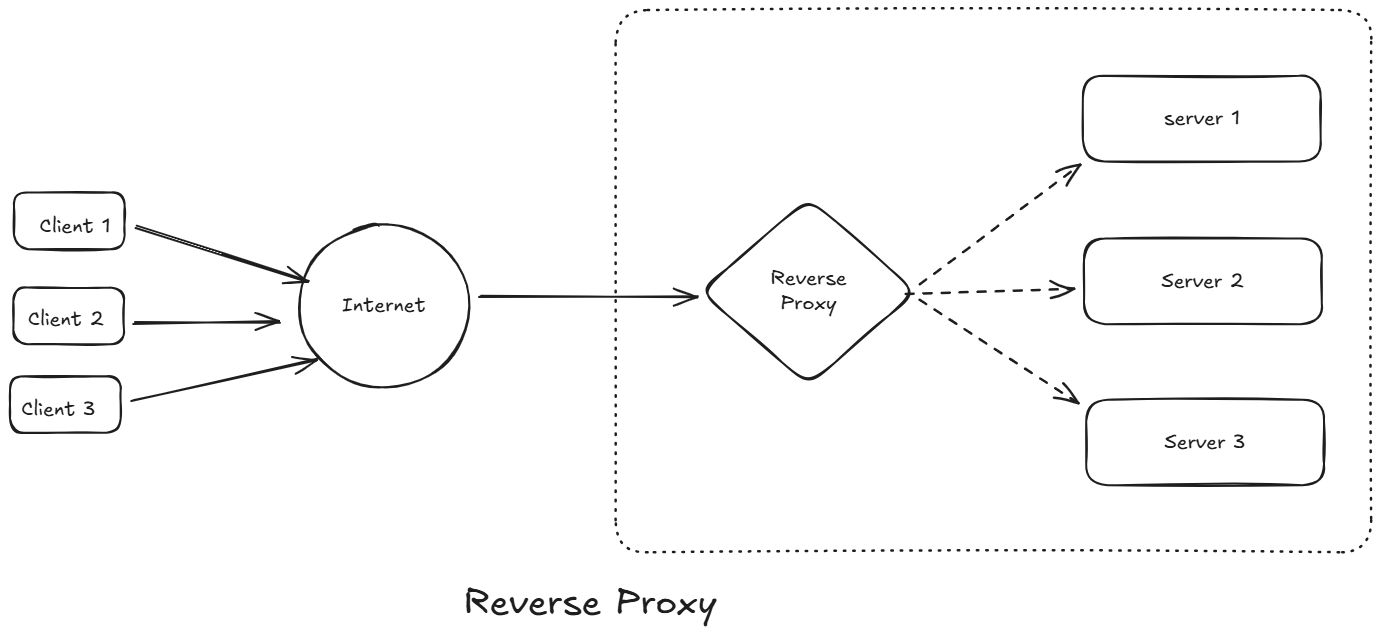
Use Cases:
- Load Balancing: Distributing incoming traffic across multiple servers.
- Security: Protecting backend servers from direct exposure and attacks.
- SSL Termination: Offloading encryption/decryption tasks from the backend servers.
- Caching: Serving cached content to reduce server load and improve response times.
Why Do We Need a Reverse Proxy?
1 Load Balancing
Most common reason.
Reverse proxy distributes traffic to multiple backend servers.
2 SSL/TLS Termination
Handling HTTPS encryption is CPU-expensive.
Reverse proxy terminates SSL = decrypt HTTPS -> send plaintext to backend via HTTP.
Benefits:
- Backend servers becomes simpler
- Centralized certificate management
- Reduced CPU usage on application servers
3 Caching
Reverse proxy can cache dynamic or semi-static content.
Examples:
- CDN edges
- NIGINX micro-caches
- Varnish cache layer
Huge speedup for high-traffic sites.
4 Security Layer / WAF
Reverse proxy protects servers by:
- Blocking bad IPs
- SQL injection detection
- DDoS protection
- Rate limiting
- Bot detection
Cloudflare & AWS Shield = giant reverse proxy networks.
5 Compression & Optimization
Reverse proxy handles:
- Gzip/Brotli compression
- Content minification
- image resizing (e.g., Cloudflare Images)
6 Routing & API Gateway
Reverse proxy can route paths to different services:
/auth -> Auth service
/payment -> Payment service
/orders -> Order serviceThis is how API gateways (kong, Apigee, NGINX, Envoy) work.
7 Service Discovery in Microservices
Reverse proxies often integrate with:
- Consul
- Eureka
- Kubernetes
So traffic always goes to healthy backend instances.
8 Zero-downtime Deployments
Reverse proxies support:
- Blue/Green deployments
- Canary releases
- A/B testing
Client never knows servers are changing behind the proxy.
Reverse Proxy vs Load Balancer
A reverse proxy and a load balancer may seem similar, but they server different primary purposes. A load balancer is mainly useful when there are multiple backend servers, as its job is to distribute incoming traffic across servers that typically perform the same function. In contrast, a reverse proxy can be valuable even with a single web or application server, since it focuses on request handling, security, caching, and routing rather than traffic distribution alone. While a reverse proxy can configured to act as a load balancer, the reverse is generally not true – a load balancer cannot fully replace the capabilities of a reverse proxy.
Note:
Isn't the reverse proxy similar to a load balance?
Both load balancers and reverse proxies act as intermediaries between clients and servers, but they serve slightly different purposes:
- Load Balancer:
Its main function is to distribute incoming traffic across multiple backend servers that serve the same purpose. This ensures high availability and scalability by preventing any single server from becoming overloaded. Load balancers use various algorithms (such as round robin, least connections, etc.) to decide how to route requests among a group of servers. - Reverse Proxy:
A reverse proxy also sits between the client and the server, but it can provide a broader set of functionalities. It can be used with a single server to improve security, perform SSL termination, cache content, and compress data, in addition to possibly balancing load. When deployed in front of multiple servers, a reverse proxy can also perform load balancing tasks.- A reverse proxy can also act as a load balancer but not the vice verse.
Forward Proxy vs Reverse Proxy
| Characteristics | Forward Proxy | Reverse Proxy |
| Position | In front of the client | In front of the server |
| Primary Goal | Protect and assist clients | Protect and optimize backend servers |
| Identity | Client's IP is hidden from the server | Server's IP is hidden from the client |
Disadvantages of Proxy Servers
Proxy servers add a lot of benefits, but they also introduce complexity, overhead, and risks.
1 Single Point of Failure (SPOF)
If your entire system's traffic depends on a proxy and it goes down:
- No traffic reaches the backend
- All services become unavailable
- Users face downtime instantly
This is why:
- Reverse proxies must be deployed in clusters
- Use health checks, failover, floating IPs, and multiple availability zones
If misconfigured -> complete outage
2 Latency Overhead
A proxy adds an extra “hop” between client and server.
Every request becomes:
Client → Proxy → Server
Instead of:
Client → Server
This adds:
- Network latency
- Processing time (routing, filtering, TLS termination)
- Queueing delays.
In high-traffic systems, this overhead can become significant.
3 Cache Inconsistency Problems
In forward or reverse proxies that cache:
- Cached content may become stale
- Users may see old state
- Updated may not appear instantly
- Improper cache invalidation = broken UI or incorrect API responses
This is a big challenge in CDNs and large-scale caching architectures.
4 Extra Infrastructure Cost
Proxies require:
- More servers
- Fault tolerance clusters
- Multiple instances behind load balancers
- Monitoring tools
- Maintenance
- Certificates and key rotations
This increases operational cost.
5 Dependencies on Vendor or Proxy Behavior
If using NGINX / Envoy / HAProxy / Cloudflare:
- You depend on their internal rules
- Updates can break routing
- Limits of the proxy become limits of your system
- Vendor outages (like Cloudflare) can take your service down.
This creates system coupling.
6 Complexity in Configuration and Management
Proxy servers require complex configuration:
- Routing rules
- TLS certificates
- CORS rules
- Path rewriting
- Caching policies
- Authentication layers
- Firewall
Leave a comment
Your email address will not be published. Required fields are marked *
